Encrypted communication & highly secure file transfers based on military standards
Tap-proof and forgery-proof communication for everyone. Intuitive – straightforward – timesaving.
The usage of conventional high performance encryption technology in mediums of communication has so far suffered from its own complexity and the difficulties that come with it for the user. Day in, day out one has to take notice of new scandals concerning data and cases of industrial espionage. The financial losses, which are caused by these incidents, often run into millions. A groundbreaking encryption-portfolio has been developed through extensive research over the time span of ten years. This portfolio can easily withstand even the severest attacks of highly equipped organizations and is simultaneously unrivaled regarding ergonomics and usability.
Communication in stealth mode
100% Protection
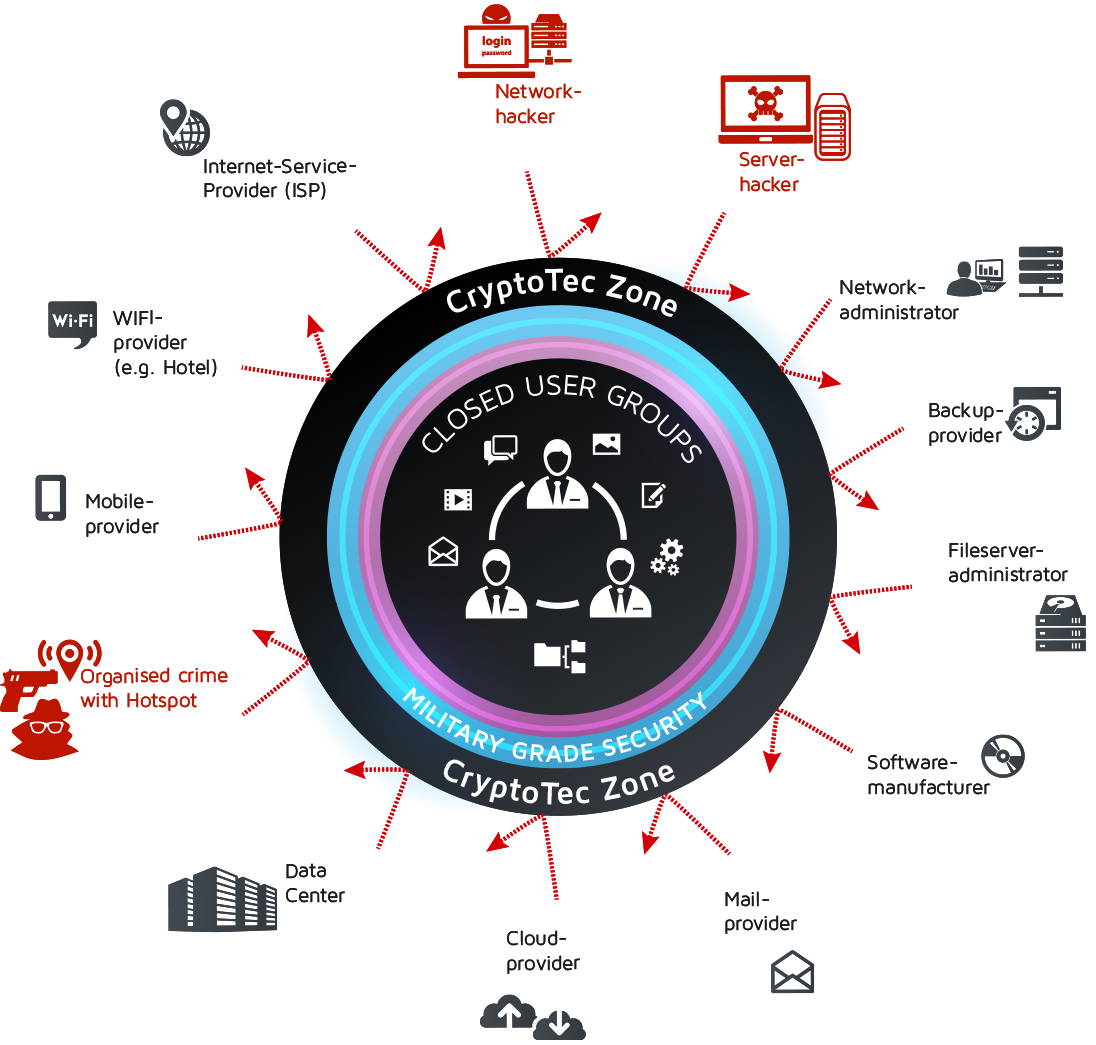
The CryptoTec Zone offers 100% protection against any unauthorized access
What makes CryptoTec Zone so secure?
CryptoID - native electronic identity card
– Generate unique cryptographic digital identity
that offers effective protection against
identity theft and forgery
– Digital signatures authenticate all users sending
and receiving data to eliminate the risk
of security breaches
CryptoTec Messenger - rapid, secure exchange of information
– Fastest way of communication
– Perfect for quick exchange
CryptoTec Transfer - drag-and-drop data transfers worldwide
– Easy drag-and-drop
– Both peer-to-peer and via servers
– Files of any size can be dispatched (quota
– control)
– High-speed transfers
– Ideal for worldwide dispatch of large data
CryptoTec Workroom — a virtual working space
– Shared processing of documents
– Authenticated protocol of all changes
– Access and processing using known programs
– Perfect for location-independent teamwork involving confidential documents
This is what makes CryptoTec Zone so secure
Encrypted with military standars
CryptoTec Zone relies on techniques of encryption which correspond to the highest military standards and cannot be cracked such as RSA-4096 unsymmetrical encryption, AES 256 symmetrical encryption and SHA-256 cryptographic hash-functions.
Integrity
CryptoTec Zone checks transferred data/messages for manipulations and uncovers them.
Regular Pentests
To verify our software's security we regularly hire external security companies to run penetration tests.
End-to-end encryption
We transfer your files encrypted from one end to any other given end via a secure transmission channel with protection against forgery.
Interception protection
The connection with CryptoTec Zone ensures the highest degree of protection from interception thru our guaranteed encryption, the transmission channel system and the device-dependent key generation.
Authenticity
All senders are confirmed via digital and device-dependent signatures and therefore send/receive all data secure and are thus protected from fraud or any kind of forgery.
